Official (ISC)2 Certified in Cybersecurity (CC) Self-Paced Training.(Chapter 5: Security Operations)
Chapter 5: Security Operations
Chapter 5 Agenda
Module 1: Understand Data Security (D5.1)
Module 2: Understand System Hardening (D5.2)
Module 3: Understand Best Practice Security Policies (D5.3)
Module 4: Understand Security Awareness Training (D5.3, D5.4)
Chapter 5 Overview
Let’s take a more detailed look at the day-to-day, moment-by-moment active use of the security controls and risk mitigation strategies that an organization has in place. We will explore ways to secure the data and the systems they reside on, and how to encourage secure practices among people who interact with the data and systems during their daily duties.
Learning Objectives
Domain 5: Security Operations Objectives
After completing this chapter, the participant will be able to:
L5
Explain concepts of security operations.
L5.1.1
Discuss data handling best practices.
L5.1.2
Identify important concepts of logging and monitoring.
L5.1.3
Summarize the different types of encryption and their common uses.
L5.2.1
Describe the concepts of configuration management.
L5.3.1
Explain the application of common security policies.
L5.4.1
Discuss the importance of security awareness training.
L5.5.1
Practice the terminology of and review the concepts of network operations.
Chapter at a Glance
While working through Chapter 5, Security Operations, make sure to:
- Complete the Knowledge Check: Logging
- Complete the Knowledge Check: Privacy Policy
- Complete the Knowledge Check: Change Management Policy
- View the Chapter 5 Summary
- Take the online Chapter 5 Quiz
- View the Terms and Definitions
Module 1: Understand Data Security
Domain D5.0, D5.1.1, D5.1.2, D5.1.3
Module Objective
- L5.0 Explain concepts of security operations.
- L5.1.1 Discuss data handling best practices.
- L5.1.2 Identify key concepts of logging and monitoring.
- L5.1.3 Summarize the different types of encryption and their common uses
Hardening is the process of applying secure configurations (to reduce the attack surface) and locking down various hardware, communications systems and software, including the operating system, web server, application server and applications, etc. In this module, we will introduce configuration management practices that will ensure systems are installed and maintained according to industry and organizational security standards.
Manny: It's hard to imagine the sheer volume of data that's flying around the world right now.
Tasha: Right, and information security, as a process and discipline, provides a structure for protecting
the value of data. As an organization creates, stores, shares, uses, modifies, archives, and finally
destroys that data.
Manny: Writing information down on paper, a whiteboard, or a flash drive, or putting it in a file on
Cloud creates data that is a tangible asset. The organization has to protect both the ideas and the
data.
Tasha: Yes, and all the copies of it in papers, books, conversation logs, computer files, database
records and the network packets which help move that information from one location or user to
another.
Manny: Wow, that's an important job.
Tasha: It sure is.
Data Handling
Data itself goes through its own life cycle as users create, use, share and modify it. Many different models of the life of a data item can be found, but they all have some basic operational steps in common. The data security life cycle model is useful because it can align easily with the different roles that people and organizations perform during the evolution of data from creation to destruction (or disposal). It also helps put the different data states of in use, at rest and in motion, into context. Let’s take a closer look.
All ideas, data, information or knowledge can be thought of as going through six major sets of activities throughout its lifetime. Conceptually, these involve:
Select a hot spot to learn more.
Create
Creating the knowledge, which is usually tacit knowledge at this point.Store
Storing or recording it in some fashion (which makes it explicit).Use
Using the knowledge, which may cause the information to be modified, supplemented or partially deleted.Share
Sharing the data with other users, whether as a copy or by moving the data from one location to another.Archive
Archiving the data when it is temporarily not needed.Destroy
Destroying the data when it is no longer needed.Data Handling Deeper Dive
need to protect, we need to make sure we know the best practices for handling this data.
First, we need to recognize which assets we need to protect. This is based on the value of the
data according to the owner of that data. Based on that, we see what kind of risk we are facing
with respect to the likelihood that this information could be compromised, destroyed or
changed by any means, and what vulnerabilities exist that we need to account for. This is the
life cycle of data handling, from create, to store, to use, to share, to archive and finally to
destroy. And at any point there are different risks to the data and different practices for
handling it. Some of these procedures are mandated by government standards.
For example, in the US, the Occupational Safety and Health Administration (OSHA) is the federal
government agency that protects the well-being of workers. Under the rules of the Healthcare
Insurance Portability and Accountability Act (HIPAA), medical records need to be kept for 10
years, but under OSHA, if we have a medical record of an on-the-job injury, that record needs
to be maintained for over 30 years, even after the last day of work in that particular
organization. That’s a regulatory requirement, and if you don’t know that or don’t abide by it,
you can find yourself in trouble as the result of an audit. So you can see that we have to be very
cautious when deciding how to handle data, as there may be multiple regulations that apply to
a single piece of data.
Also in the US there are also specific guidelines related to the Payment Card Industry Data
Security Standards (PCI DSS) requirements regarding credit card information and how to
maintain that information securely. In the European Union, the GDPR also has specific
requirements regarding the handling of financial data. In order to protect the data properly,
you need to know all the relevant requirements for the type of data being protected in the
various geographic areas.
Many countries and other jurisdictions have regulations that require certain data protections
throughout every stage of the data’s life cycle. These govern how the data is acquired,
processed, stored, and ultimately destroyed. And when looking at the life cycle of the data, we
need to keep a watchful eye and protect the information at every stage, even if it’s ready to be
legally destroyed at the end of the life cycle. In some cases, multiple jurisdictions may impose
rules affecting the data we are charged with protecting. In these instances, we need to be
aware of any and all regulations that affect us.
Some data handling practices include classification and labeling, where you determine the
sensitivity of the data, what is available to everyone and what needs to be restricted, and label
the information accordingly so that your access controls will allow the correct level of access.
Retention is how long we store the information and where, based on the requirements of our
organization and perhaps regulatory agencies as well. And then there needs to be defensible
destruction, meaning that we have the regulatory mandate backing up our decision to destroy
the data. Destruction can be physical, of hard drives or computer chips, or destruction of digital
records, which can be done under a number of methodologies. We need to make sure we understand the secure destruction of the data, because often we think we can just empty the
virtual trash can to delete the data. But when we do that, old emails and other data may never
be erased. To completely erase the data on physical media, you need to use some technical
equipment for degaussing, such as powerful magnets to erase the data stored on tape and disk
media such as computer and laptop hard drives, diskettes, reels, cassettes and cartridge tapes.
However, an individual with sophisticated equipment could potentially still retrieve that
information, at least partially. So we must make sure we understand what recovery tools are
available, because if you are subject to regulatory compliance, you have to follow through with
specific protocols and processes to destroy that information as required so that it can no longer
be accessed in any way.
Logging and Monitoring Security Events
Logging is the primary form of instrumentation that attempts to capture signals generated by events. Events are any actions that take place within the systems environment and cause measurable or observable change in one or more elements or resources within the system. Logging imposes a computational cost but is invaluable when determining accountability. Proper design of logging environments and regular log reviews remain best practices regardless of the type of computer system.
Major controls frameworks emphasize the importance of organizational logging practices. Information that may be relevant to being recorded and reviewed include (but is not limited to):
- user IDs
- system activities
- dates/times of key events (e.g., logon and logoff)
- device and location identity
- successful and rejected system and resource access attempts
- system configuration changes and system protection activation and deactivation events
Logging and monitoring the health of the information environment is essential to identifying inefficient or improperly performing systems, detecting compromises and providing a record of how systems are used. Robust logging practices provide tools to effectively correlate information from diverse systems to fully understand the relationship between one activity and another.
Log reviews are an essential function not only for security assessment and testing but also for identifying security incidents, policy violations, fraudulent activities and operational problems near the time of occurrence. Log reviews support audits – forensic analysis related to internal and external investigations – and provide support for organizational security baselines. Review of historic audit logs can determine if a vulnerability identified in a system has been previously exploited.
It is helpful for an organization to create components of a log management infrastructure and determine how these components interact. This aids in preserving the integrity of log data from accidental or intentional modification or deletion and in maintaining the confidentiality of log data.
Controls are implemented to protect against unauthorized changes to log information. Operational problems with the logging facility are often related to alterations to the messages that are recorded, log files being edited or deleted, and storage capacity of log file media being exceeded. Organizations must maintain adherence to retention policy for logs as prescribed by law, regulations and corporate governance. Since attackers want to hide the evidence of their attack, the organization’s policies and procedures should also address the preservation of original logs. Additionally, the logs contain valuable and sensitive information about the organization. Appropriate measures must be taken to protect the log data from malicious use.
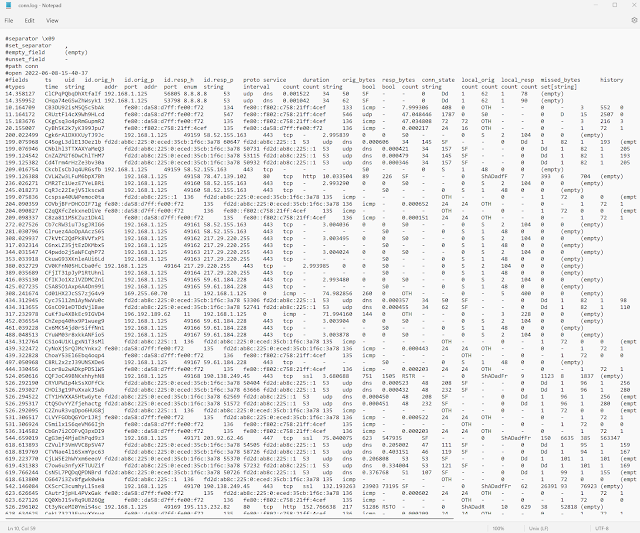
EVENTS

EVENT DETAIL

RAW LOG(also show in bottom of event detail)
Data Security Event Example
Here is a data security event example. It’s a raw log, and it is one way to see if someone tried to break into a secure file and hijack the server. Of course, there are other systems now that are a little more user-friendly. But security engineers get very familiar with some of these codes and can figure out exactly who was trying to log it, was it a secure port or a questionable port that they were trying to use to penetrate our site.
Information security is not something that you just plug in as needed. You can have some patching on a system that already exists, such as updates, but if you don’t have a secure system, you can’t just plug in something to protect it. From the very beginning, we need to plan for that security, even before the data is introduced into the network.
Event Logging Best Practices
Different tools are used depending on whether the risk from the attack is from traffic coming into or leaving the infrastructure. Ingress monitoring refers to surveillance and assessment of all inbound communications traffic and access attempts. Devices and tools that offer logging and alerting opportunities for ingress monitoring include:
- Firewalls
- Gateways
- Remote authentication servers
- IDS/IPS tools
- SIEM solutions
- Anti-malware solutions
Egress monitoring is used to regulate data leaving the organization’s IT environment. The term currently used in conjunction with this effort is data loss prevention (DLP) or data leak protection. The DLP solution should be deployed so that it can inspect all forms of data leaving the organization, including:
- Email (content and attachments)
- Copy to portable media
- File Transfer Protocol (FTP)
- Posting to web pages/websites
- Applications/application programming interfaces (APIs)
Encryption Overview
Almost every action we take in our modern digital world involves cryptography. Encryption protects our personal and business transactions; digitally signed software updates verify their creator’s or supplier’s claim to authenticity. Digitally signed contracts, binding on all parties, are routinely exchanged via email without fear of being repudiated later by the sender.
Cryptography is used to protect information by keeping its meaning or content secret and making it unintelligible to someone who does not have a way to decrypt (unlock) that protected information. The objective of every encryption system is to transform an original set of data, called the plaintext, into an otherwise unintelligible encrypted form, called the ciphertext.
Properly used, singly or in combination, cryptographic solutions provide a range of services that can help achieve required systems security postures in many ways:
- Confidentiality: Cryptography provides confidentiality by hiding or obscuring a message so that it cannot be understood by anyone except the intended recipient. Confidentiality keeps information secret from those who are not authorized to have it.
- Integrity: hash functions and digital signatures can provide integrity services that allow a recipient to verify that a message has not been altered by malice or error. These include simple message integrity controls. Any changes, deliberate or accidental, will result in the two results (by sender and by recipient) being different.
Encryption Overview
An encryption system is the set of hardware, software, algorithms, control parameters and operational methods that provide a set of encryption services.
Plaintext is the data or message in its normal, unencrypted form and format. Its meaning or value to an end user (a person or a process) is immediately available for use.
Plaintext can be:
- image, audio or video files in their raw or compressed forms
- human-readable text and numeric data, with or without markup language elements for formatting and metadata
- database files or records and fields within a database
- or anything else that can be represented in digital form for computer processing, transmission and storage
It is important to remember that plaintext can be anything—much of which is not readable to humans in the first place.
Symmetric Encryption
The central characteristic of a symmetric algorithm is that it uses the same key in both the encryption and the decryption processes. It could be said that the decryption process is just a mirror image of the encryption process. This image displays how symmetric algorithms work.
The same key is used for both the encryption and decryption processes. This means that the two parties communicating need to share knowledge of the same key. This type of algorithm protects data, as a person who does not have the correct key would not be able to read the encrypted message. Because the key is shared, however, this can lead to several other challenges:
- If two parties suspect a specific communication path between them is compromised, they obviously can't share key material along that path. Someone who has compromised communications between the parties would also intercept the key.
- Distribution of the key is difficult, because the key cannot be sent in the same channel as the encrypted message, or the man-in-the-middle (MITM) would have access to the key. Sending the key through a different channel (band) than the encrypted message is called out-of-band key distribution. Examples of out-of-band key distribution would include sending the key via courier, fax or phone.
- Any party with knowledge of the key can access (and therefore change) the message.
- Each individual or group of people wishing to communicate would need to use a different key for each individual or group they want to connect with. This raises the challenge of scalability — the number of keys needed grows quickly as the number of different users or groups increases. Under this type of symmetric arrangement, an organization of 1,000 employees would need to manage 499,500 keys if every employee wanted to communicate confidentially with every other employee.
Encryption Deeper Dive
depictions by cave dwellers of Magura Cave in Bulgaria to the Pyramids at Giza. Even then, each
group had its own primitive cryptographic approach, so that members of the tribe or group
could communicate with one another while keeping secrets from the rival tribes regarding
hunting grounds or sources of water and food.
It is part of human nature to encrypt information. You start with clear text, which is the
information that you and I could easily read, and then you use an algorithm, which is often a
form of software that can be embedded in the system. But that needs to be activated with an
encryption key. A very simple example is if you are trying to encrypt a PDF document; for
example, perhaps your accountant is sending you some documents to sign before submitting
your taxes. Encryption would create a ciphertext, which no one can use, and you and your
accountant would have set up a preset encryption key so that you could retrieve the
information at either end of the communication. You need to have good key management,
which means you safeguard the information, because imagine if you have thousands of keys in
a commercial environment. There is often a third party or external server where the keys will
be separately stored and managed, so you don’t have all your eggs in one basket, so to speak. It
will be protected through a hashing system, which we will explore in a moment, and no one
else can have access to those keys.
Asymmetric encryption is more secure because the sender and receiver each uses a unique
code, often a certificate, so you can confirm that the information has been sent from the
sender to the recipient in a secure manner.
Module 2: Understand System Hardening
Domain D5.2.1
Module Objective
- L5.2.1 Describe the concepts of configuration management.
Manny: With so much data to work with, and so many different software applications required
to handle it, how do companies keep track of everything?
Tasha: It's a challenge all right, that's why we need configuration management. It's part of
cybersecurity in that it protects the confidentiality, integrity, and availability of data by making sure
that only authorized and validated changes are made to a system. Every change also needs to be
tested to make sure it doesn't cause any disruption to any other part of the system.
Manny: I can understand that. It seems like every time we upgrade our computer systems at the high
school, something else stops working.
Tasha: Let's find out how cybersecurity professionals work to prevent that from happening.
Configuration Management Overview
The Risks of Change
sure you test in model environments before you make any change in a production or live
environment. Even with extensive planning and testing, there are sometimes unintended
consequences, so you must make sure there is a rollback plan. A rollback is restoring the system
to the state it was in before the change was made. To the point where we know it was working
properly before we introduced changes into the environment. We need to make sure we
review and test all the patches and can restore the previous configuration.
Maintaining a separate testing environment can be a logistical challenge for many
organizations; as such, many do not have separate production and testing environments to
properly vet all patches and system updates. In this case, they may rely on vendor third party
testing to certify a new software release based on a generic set of data. The rollback plan is
important in all environments, but it is absolutely critical in those who are unable to fully test a
change.
Module 3: Understand Best Practice Security Policies
Domain D5.3, D5.3.1, D5.3.2, D5.3.3, D5.3.4, D5.3.5, D5.3.6
Module Objective
- L5.3.1 Explain the application of common security policies.
An organization’s security policies define what “security” means to that organization, which in almost all cases reflects the tradeoff between security, operability, affordability and potential risk impacts. Security policies express or impose behavioral or other constraints on the system and its use. Well-designed systems operating within these constraints should reduce the potential of security breaches to an acceptable level.
Security governance that does not align properly with organizational goals can lead to implementation of security policies and decisions that unnecessarily inhibit productivity, impose undue costs and hinder strategic intent.
their data?
Tasha: Policies can include password requirements, limits on personal devices, and all kinds of other
policies to ensure privacy and security. In this module, we'll explore the most common security policies
found in organizations and identify some components of these policies.
Common Security Policies
Keith Writes a Password Policy
Tasha: Sandra's having trouble logging on to her work account.
Sandra: Why won't it take my password?
Keith: Are you still using your old password?
Sandra: Yeah, it's what I always use.
Keith: Oh, that’s why. You need a new password. The old password expires after 12 weeks.
Sandra: Why did you do that? I like my password just the way it was.
Keith: It's safer. Didn't you get my email I sent yesterday, or last week, or the one the week before
that?
Sandra: Hey, I thought it was for employees. I'm the owner. I'm not an employee.
Keith: It's for everybody, including you. Let me show you how to reset your password.
Sandra: Oh, you just do it for me. My password is ‘1234.’
Keith: Not anymore it isn't. We had to increase our requirements to help keep the bad guys out. And as
the owner, your account is more valuable than the rest of the employees. New passwords have to have
at least eight characters, upper and lower case, plus a number and a special character, like an
exclamation point or a question mark.
Sandra: Goodness – um, just make it ‘Keith1234.’
Keith: Yeah!
Sandra: Question mark.
Keith: Nobody’s going to guess that.
Change Management Components
Change Management Components in the Workplace
Narrator: Change management happens in a cycle. There is no real stopping point; it is
continuously going. This means that there must be continuous monitoring of that environment.
So, if you or anyone should request a change, it needs to go through the appropriate approvals.
The organization must be prepared for rollback if necessary, meaning that if that particular
change did not work, we need to be able to roll back to the legacy system.
While change management is an organization-wide process, it often falls on Information
Security professionals to coordinate the effort and maybe to provide oversight and governance.
Depending on the size of the organization, it may also fall under an IT or development area. In
organizations that have a quality or risk management department, it would be a great fit in
either of those areas too. The common theme is that change management acknowledges and
incorporates input from the end users as well as all areas of IT, Development, Information
Security and most importantly Management, to ensure that all changes are properly tested,
approved and communicated prior to being implemented.
Privacy Policy
Some organizations encourage employees to make wide personal use of the organization’s IT
assets, to improve morale and reduce interruptions between the user’s personal life and work.
Some organizations encourage users to use organizational assets to perform personal
educational tasks, as well—this way, the employee gets the benefit of the assets, and the
organization gets a higher-trained and happier employee. Some organizations severely limit
users' personal use of IT assets, in order to reduce risk within the organization.
All security related policies should align with the organization’s risk tolerance while ensuring
that regulatory requirements are met. An organization that does not store confidential data on
a laptop or workstation is likely to be more relaxed in their acceptable use policy, while a
healthcare facility, research institution or defense contractor may be much stricter, as they
have data that can be potentially devastating if compromised.
Module 4: Understand Security Awareness Training
Domain D5.4, D5.4.1, D5.4.2, D5.3.2
Module Objective
- L5.4.1 Discuss the importance of security awareness training.
To reduce the effectiveness of certain types of attacks (such as social engineering), it is crucial that the organization informs its employees and staff how to recognize security problems and how to operate in a secure manner. While the specifics of secure operation differ in each organization, there are some general concepts that are applicable to all such programs.
Manny: So what's the most important tool for cybersecurity, Tasha?
Tasha: I'd say the most important tool is your human resources—your people.
Manny: People more so than technology, firewalls, passwords, and all that stuff?
Tasha: Yes, Manny. It's people who develop that technology, install those firewalls, create those
passwords. Even more so, everyone must follow best practices and policies to ensure the secure
handling of the data they work with every day. That's why security awareness training is so important.
Your people must know what to look for and what to do when they see it. They must stay vigilant.
Complacency is the enemy when it comes cybersecurity.
Manny: If you see something, say something.
Tasha: Exactly. Let's find out more.
Purpose
The purpose of awareness training is to make sure everyone knows what is expected of them, based on responsibilities and accountabilities, and to find out if there is any carelessness or complacency that may pose a risk to the organization. We will be able to align the information security goals with the organization’s missions and vision and have a better sense of what the environment is.
What is Security Awareness Training?
Let’s start with a clear understanding of the three different types of learning activities that organizations use, whether for information security or for any other purpose:
- Education: The overall goal of education is to help learners improve their understanding of these ideas and their ability to relate them to their own experiences and apply that learning in useful ways.
- Training: Focuses on building proficiency in a specific set of skills or actions, including sharpening the perception and judgment needed to make decisions as to which skill to use, when to use it and how to apply it. Training can focus on low-level skills, an entire task or complex workflows consisting of many tasks.
- Awareness: These are activities that attract and engage the learner’s attention by acquainting them with aspects of an issue, concern, problem or need.
You’ll notice that none of these have an expressed or implied degree of formality, location or target audience. (Think of a newly hired senior executive with little or no exposure to the specific compliance needs your organization faces; first, someone has to get their attention and make them aware of the need to understand. The rest can follow.)
The One That Got Away
Gabriela: So, something really weird happened. I got a text this morning saying that I won
$1000 from Amazon.
Keith: Wow. Did you respond?
Gabriela: Well, I was going to, but then at the last minute I noticed that it was from Amazoon,
not Amazon. I mean, a company wouldn't misspell its own name, would it? And then it got me
thinking about that one time that I accidentally downloaded a virus, and I thought that I would
just wait to talk to you about it, since I know you've been studying cybersecurity and phishing
and all that.
Keith: Congrats You passed. That was a fake link I sent you to see if you would click on it.
Gabriela: (sighs) Well, I guess that security awareness training you've been doing has finally
paid off. But I still kind of feel like someone owes me $1,000.
(People chattering)
Tasha: Susan arrives at the coffee shop in time to hear Keith and Gabrielle's conversation.
(People chattering)
Susan: Well, look at how far you've come since we first started talking about cybersecurity.
Keith: Well, at first I figured I didn't have the technical skills.
Susan: Ah, but what it really comes down to is you have curiosity, and you're a good
communicator, and you work well as part of a team. You're also analytical. You're good at
identifying patterns, you know, seeing the bigger picture, but also the smaller details. You are
actually perfect for cybersecurity work.
Keith: I guess it is pretty interesting, understanding data and how to keep people's data safe.
Susan: And it's always changing. There are so many opportunities in this field and different
directions you can take. I'm proud to say that I am a System Security Certified Practitioner, and
I'm even thinking about earning my CISSP from (ISC)2.
Keith: What's that?
Susan: It's a Certified Information System Security Professional, a globally recognized
cybersecurity certification.
Keith: Wow, that is so cool. It seems like cybersecurity never gets boring or stale. I'd always be
growing, unlike here.
Susan: Hey, do not let your mom hear you say that. she has coffee running in her veins.
Keith: Gabriela can take over for me, right? I mean, you know more about customers' data and
how to keep it safe.
Gabriela: I mean, that would be great, Keith, but I might consider a future in cybersecurity
myself.
Keith: I'm ready to start now. What do I need to do to get a job like yours?
Susan: I might just be able to point you in the right direction. What have we got here?
Keith: Oh, we're working on...
Security Awareness Training Examples
Let’s look at an example of security awareness training by using an organization’s strategy to improve fire safety in the workplace:
- Education may help workers in a secure server room understand the interaction of the various fire and smoke detectors, suppression systems, alarms and their interactions with electrical power, lighting and ventilation systems.
- Training would provide those workers with task-specific, detailed learning about the proper actions each should take in the event of an alarm, a suppression system going off without an alarm, a ventilation system failure or other contingency. This training would build on the learning acquired via the educational activities.
- Awareness activities would include not only posting the appropriate signage, floor or doorway markings, but also other indicators to help workers detect an anomaly, respond to an alarm and take appropriate action. In this case, awareness is a constantly available reminder of what to do when the alarms go off.
Translating that into an anti-phishing campaign might be done by:
- Education may be used to help select groups of users better understand the ways in which social engineering attacks are conducted and engage those users in creating and testing their own strategies for improving their defensive techniques.
- Training will help users increase their proficiency in recognizing a potential phishing or similar attempt, while also helping them practice the correct responses to such events. Training may include simulated phishing emails sent to users on a network to test their ability to identify a phishing email.
- Raising users’ overall awareness of the threat posed by phishing, vishing, SMS phishing (also called “smishing) and other social engineering tactics. Awareness techniques can also alert selected users to new or novel approaches that such attacks might be taking.
Let’s look at some common risks and why it’s important to include them in your security awareness training programs.
Phishing
The use of phishing attacks to target individuals, entire departments and even companies is a significant threat that the security professional needs to be aware of and be prepared to defend against. Countless variations on the basic phishing attack have been developed in recent years, leading to a variety of attacks that are deployed relentlessly against individuals and networks in a never-ending stream of emails, phone calls, spam, instant messages, videos, file attachments and many other delivery mechanisms.
Phishing attacks that attempt to trick highly placed officials or private individuals with sizable assets into authorizing large fund wire transfers to previously unknown entities are known as whaling attacks .
Social Engineering
Social engineering is an important part of any security awareness training program for one very simple reason: bad actors know that it works. For the cyberattackers, social engineering is an inexpensive investment with a potentially very high payoff. Social engineering, applied over time, can extract significant insider knowledge about almost any organization or individual.
One of the most important messages to deliver in a security awareness program is an understanding of the threat of social engineering. People need to be reminded of the threat and types of social engineering so that they can recognize and resist a social engineering attack.
Most social engineering techniques are not new. Many have even been taught as basic fieldcraft for espionage agencies and are part of the repertoire of investigative techniques used by real and fictional police detectives. A short list of the tactics that we see across cyberspace currently includes:
- Phone phishing or vishing: Using a rogue interactive voice response (IVR) system to re-create a legitimate-sounding copy of a bank or other institution’s IVR system. The victim is prompted through a phishing email to call in to the “bank” via a provided phone number to verify information such as account numbers, account access codes or a PIN and to confirm answers to security questions, contact information and addresses. A typical vishing system will reject logins continually, ensuring the victim enters PINs or passwords multiple times, often disclosing several different passwords. More advanced systems may be used to transfer the victim to a human posing as a customer service agent for further questioning.
- Pretexting: The human equivalent of phishing, where someone impersonates an authority figure or a trusted individual in an attempt to gain access to your login information. The pretexter may claim to be an IT support worker who is supposed to do maintenance or an investigator performing a company audit. Or they might impersonate a coworker, the police, a tax authority or some other seemingly legitimate person. The goal is to gain access to your computer and information.
- Quid pro quo: A request for your password or login credentials in exchange for some compensation, such as a “free gift,” a monetary payment or access to an online game or service. If it sounds too good to be true, it probably is.
- Tailgating: The practice of following an authorized user into a restricted area or system. The low-tech version of tailgating would occur when a stranger asks you to hold the door open behind you because they forgot their company RFID card. In a more sophisticated version, someone may ask to borrow your phone or laptop to perform a simple action when he or she is actually installing malicious software onto your device.
Social engineering works because it plays on human tendencies. Education, training and awareness work best to counter or defend against social engineering because they help people realize that every person in the organization plays a role in information security.
Password Protection
We use many different passwords and systems. Many password managers will store a user’s passwords for them so the user does not have to remember all their passwords for multiple systems. The greatest disadvantage of these solutions is the risk of compromise of the password manager.
These password managers may be protected by a weak password or passphrase chosen by the user and easily compromised. There have been many cases where a person’s private data was stored by a cloud provider but easily accessed by unauthorized persons through password compromise.
Organizations should encourage the use of different passwords for different systems and should provide a recommended password management solution for its users.
Examples of poor password protection that should be avoided are:
- Reusing passwords for multiple systems, especially using the same password for business and personal use.
- Writing down passwords and leaving them in unsecured areas.
- Sharing a password with tech support or a co-worker.
Password Advice and Examples
Narrator: Going back to the subject of the password. If you have a 10-number password, then
with software with the cryptographic calculation to brute force attack your environment, it will
take 5 seconds to crack. Most people think 8 characters with multiple different characters is
pretty secure, and that’s kind of standard for password requirements. But if someone really
wants it, it may take them 35 days. We’d rather be more secure than that.
If you have 16 characters with one upper case and one special character, for example, this is
more secure, because you have upper and lowercase characters and special characters. To
crack this, it will take about 152,000 years.
So just by following a good password policy and appropriate procedures, we can improve our
password security immensely.
Best Practices of Security Awareness Training
Narrator: We have to make sure we have appropriate communications about current and
potential threats to keep awareness high. We could even encourage friendly competition
between departments to spot the most phishing attempts. We can offer friendly reminders, like
a little squishy stress ball that says, “Lock your computer.” There are also automatic systems
that lock the computer automatically when you step away.
It is important to make sure we get positive feedback about our training, ensuring it is
appropriate and understood. Make sure the organization’s leaders understand the importance
of training and working to promote and improve the information security environment of the
organization. And provide the opportunity for personnel to practice what they’ve learned, with
exercises and simulations. Occasionally send simulated phishing emails, for example, and give
them positive feedback for reporting it.
Depending on the organization’s culture and risk profile, awareness training should be a
positive experience for everyone and not punitive unless it is absolutely necessary.
Module 5: Chapter 5 Summary
Domain 5.1.1, 5.1.2, 5.1.3, 5.2.1, 5.3.1, 5.3.2, 5.3.3, 5.3.4, 5.3.6, 5.4.1, 5.4.2
Module Objective
L5.5.1 Practice the terminology and review concepts of access controls
This chapter focused on the day-to-day, moment-by-moment, use of security controls and risk mitigation strategies in an organization. We discovered ways to secure data and the systems they reside on. Data (information) security as a process and discipline provides a structure for protecting the value of data as the organization creates, stores, shares, uses, modifies, archives and finally destroys that data (known as data handling). During data handling, an organization classifies (assigns data sensitivity levels), categorizes (determines type of data), labels (applies a name to the data), retains (determines how long to keep the data) and destroys (erases or destroys) the data.
A best practice for securing data is encrypting the data. We explored the process of encrypting data in plaintext with a key and algorithm to create ciphertext then using either the same key (symmetric) or a different key (asymmetric) and same algorithm to decrypt the ciphertext to convert it back to plaintext. Then hashing was methodically described; hashing takes an input set of data (of almost arbitrary size) and returns a fixed-length result called the hash value.
System hardening is the process of applying secure configurations (to reduce the attack surface) and locking down various hardware, communications systems and software, including operating system, web server, application server, application, etc. We also discussed configuration management, a process and discipline used to ensure that the only changes made to a system are those that have been authorized and validated. Configuration management consists of identification, baseline, change control, and verification and audit. During configuration management, one must conduct inventory, baselines, updates, and patches.
The following best practice security policies were examined: data handling (appropriate use of data), password (appropriate use of passwords), acceptable use (appropriate use of the assets, devices, and data), bring your own device (appropriate use of personal devices), privacy (appropriate protection of one’s privacy), and change management (appropriate transition from current state to a future state). Change management practices address a common set of core activities: documentation, approval, and rollback. It starts with a request for change (RFC) and moves through various development and test stages until the change is released to the end users.
We ended the chapter by discussing the importance of security awareness training and how it reduces the internal threat to an organization. By breaking down the levels of security awareness training into education, training, and awareness, we identified that the training can be tailored to the security topic(s), organization, position and/or individual. The module highlighted some of the main threats, including phishing and social engineering and why it's important to include them in your security awareness training programs. We also emphasized the importance of password protection.

.png)
.png)
.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
Comments
Post a Comment